Seeing bounces or 5.7.x relay denied when you send from Microsoft 365? That usually means the send path is wrong or a required setting is missing.
Microsoft 365 supports two ways to send mail. SMTP AUTH through smtp.office365.com, and SMTP relay through a connector.
The right choice depends on your app or device, the mailbox you use, and your compliance needs.
This guide explains the exact values for server, port, TLS, and authentication.
It shows when to use SMTP AUTH or relay, the tenant limits that affect throughput, and the common error codes with fast fixes.
If SMTP is not the right fit for your scenario, you will also see safer alternatives that keep delivery reliable and compliant.
Office 365 SMTP, POP3, and IMAP Settings (Receiving vs Sending)
Use SMTP for sending mail from apps/services and IMAP/POP3 for retrieving mail into clients.
IMAP is the better choice for most users because it keeps mail and folders in sync across all devices.
POP3 is fine for simple download-and-keep workflows.
The core Office 365 SMTP settings handle outbound delivery, while IMAP (preferred) or POP3 let users read mail across devices.
| Protocol | Purpose | Server | Port | Encryption |
| SMTP | Sending | smtp.office365.com | 587 (STARTTLS) | STARTTLS |
| IMAP | Receiving | outlook.office365.com | 993 | SSL/TLS |
| POP3 | Receiving | outlook.office365.com | 995 | SSL/TLS |
Imp Notes
- SMTP is for sending from apps and services. Use smtp.office365.com on port 587 with STARTTLS and OAuth2.
- IMAP or POP3 are for receiving in mail clients. Choose IMAP if you read mail on more than one device because it keeps folders in sync.
- Modern authentication with OAuth2 is recommended. Basic authentication may be turned off by your organization.
- If a device cannot sign in, set up SMTP relay with an Exchange Online connector on port 25 and allow only your approved public IP addresses.
Office 365 SMTP Relay vs Direct SMTP Auth: Key Differences & Limits
Direct SMTP authentication uses smtp.office365.com on port 587 with STARTTLS and OAuth2. Choose this when your app can sign in.
SMTP relay through an Exchange Online connector on port 25 works for printers and other devices that cannot authenticate but send from trusted public IP addresses.
SMTP AUTH sends as the mailbox that signs in or one of its aliases, while relay can send for any accepted domain in your tenant.
Both options follow Exchange Online limits, roughly ten thousand recipients per mailbox per day and up to five hundred recipients per message.
Pick based on whether your sender can authenticate and how much control you have over the network.
Keep your settings consistent for good deliverability, watch for throttling or temporary delays, and add simple retry logic to stay within policy.
| Feature | Direct SMTP Auth (Client Submission) | Office 365 SMTP Relay (Connector) |
| Authentication | Mailbox sign-in (password or OAuth2/Modern Auth) | IP-based,no mailbox login |
| Typical use | Apps: Outlook, WordPress, CRMs, ZapMail | Devices: copiers/scanners, legacy servers |
| Port & Security | 587 with STARTTLS (core Office 365 SMTP settings) | 25 with TLS (as available) |
| Setup | Client-side configuration | Admin-created connector + approved IP(s) |
| Identities (From:) | Send as / Send on behalf (with permissions) | Any accepted domain per connector policy |
| Limits/Throttling | 30 messages/min, 10,000 recipients/day, recipient limit up to 1,000 (default often 500). | Not bound by 30/min or 10k/day, throughput is policy/reputation-based (“reasonable limits”) on connector/IP. |
How to Configure Office 365 SMTP Settings (Step-by-Step)
Step 1 Sign in to Microsoft 365 admin center
Use an account with Global or Exchange admin rights. Confirm the sender mailbox is licensed and not blocked.
Step 2 Open the mailbox settings
Go to Users then Active users. Select the mailbox. Open Mail and choose Manage email apps. This page controls protocol access for the user, including SMTP.
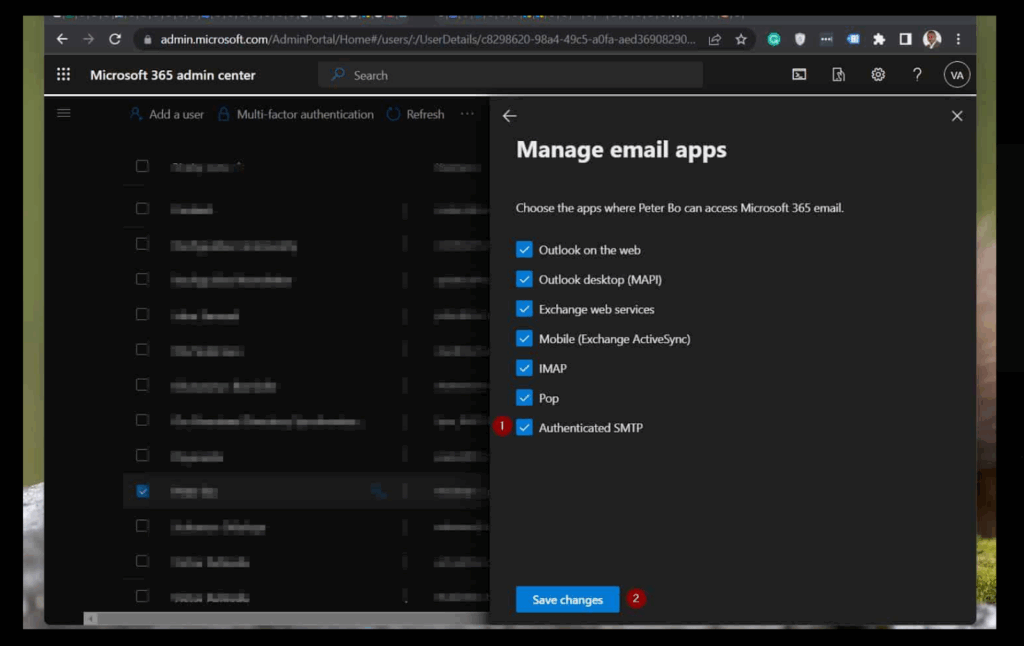
Step 3 Enable Authenticated SMTP
Turn on Authenticated SMTP and save.
If your organization has SMTP AUTH turned off globally, enabling it here allows it for this one mailbox.
Step 4 Configure your app or client
Set the server to smtp.office365.com.
Use port 587. Turn on STARTTLS. Require authentication.
Use the full email address as the username.
Use the account password or an app password when multifactor is on. Prefer OAuth2 when the client supports it.
Make sure the From address is the mailbox itself or that you have Send As permission.
Step 5 Send a test message
Send to one internal and one external address.
If delivery fails, check the port and TLS setting, the username and password, the SMTP AUTH toggle for the mailbox, and any tenant policies that might override client settings.
Use SMTP relay with a connector only for devices that cannot authenticate.
How to Configure Office 365 SMTP Relay in Admin Center (With Connector Setup)
Step 1: Open Exchange admin center
In the Exchange admin center, go to Mail flow, then Connectors, and choose Add to create a new connector for relay.
Step 2: Define the direction
Set From to Your organization’s email server and To to Office 365.
This creates an inbound connector so Microsoft 365 will accept mail from your devices or apps.
Step 3: Allow only trusted IP addresses
Choose verification by sender IP address and enter only your static public IPs.
Avoid ranges you do not control. Relay should be limited to known sources.
Step 4: Choose TLS behavior
If your device or app supports TLS, enable it for the connector.
For older hardware, keep TLS opportunistic and leave Reject if TLS fails unchecked to prevent avoidable failures.
Step 5: Scope and enable the connector
Optionally limit the connector to specific accepted domains.
Give it a clear name such as Printer Scanner Relay HQ IP, switch it on, and save.
Test the relay
Send a message from a device using your domain’s MX host on port 25 without authentication.
Then use Message trace to confirm the message flowed through the connector.
Which Port Should You Use: 25 vs 587 in Office 365 SMTP?
Use port 587 in most cases because your app can sign in with modern authentication and STARTTLS, and it is the default in Microsoft 365.
Use port 25 only when you create an Exchange Online connector for SMTP relay from a fixed, trusted public IP such as a printer or scanner on your network.
If your provider blocks port 25, choose 587.
If a device cannot authenticate, use port 25 with a tightly scoped connector.
For campaigns or app driven sending, 587provides mailbox level auditing and gentler throttling. Port 465 is not supported.
| Port | Usage | Authorisation Required | Notes |
| 587 | SMTP AUTH (client submission) | Yes | Requires STARTTLS; best for apps/clients; aligns with Modern Auth. |
| 25 | office365 smtp relay(connector) | No | For trusted static IPs; opportunistic TLS; often blocked by ISPs/hosts. |
| 465 | Deprecated | — | Not supported by Exchange Online. |
Common Office 365 SMTP Errors and Fixes (Auth, Relay, Spam, Firewall)
- Authentication failed (535 5.7.139)
Turn on Authenticated SMTP for the mailbox. Use smtp.office365.com on port 587 with STARTTLS. Sign in with OAuth2.
If multifactor is required and the client cannot use OAuth2, use an app password only if your policy allows it.
- Relay not allowed (550 5.7.1)
If the device cannot sign in, create an inbound connector for your static public IPs and send through your domain’s MX on port 25.
If the app can sign in, use SMTP AUTH on port 587.
Make sure the sender’s domain is an accepted domain in your tenant.
- Messages going to spam
Publish SPF with include:spf.protection.outlook.com.
Enable DKIM in Exchange Online. Add a DMARC record and align the From and DKIM domains.
Increase send volume gradually and keep lists clean and content consistent.
- Connection timeout or connection refused
Allow outbound connections to smtp.office365.com on port 587 and keep STARTTLS enabled.
Open port 25 only for connector based relay.
Exclude SMTP traffic from TLS inspection and check that the firewall is not blocking Microsoft 365 endpoints.
- MFA conflicts or Basic Authentication blocked
Move the client to OAuth2 (XOAUTH2).
Avoid Basic Authentication. Use app passwords only as a temporary fallback when permitted by policy.
Security and Compliance Checklist for Office 365 SMTP & Relay
Use this checklist to secure Microsoft 365 SMTP and relay, meet compliance requirements, and keep mail flowing reliably.
- Enforce TLS Everywhere
Require STARTTLS (TLS 1.2+) on port 587; disable legacy ciphers/protocols. A
void port 465 (unsupported in Exchange Online).
- Prefer OAuth2 (Modern Auth)
Block Basic Auth tenant-wide. Use XOAUTH2 with Conditional Access/MFA and rotate client secrets or certificates regularly.
- Publish SPF, Enable DKIM, Align DMARC
Include Microsoft 365 in SPF, turn on DKIM in EAC, and set DMARC to p=quarantine/reject with reporting to keep alignment tight.
- Restrict Relay by IP (Connector)
Scope office365 smtp relay to static, trusted IPs and accepted domains only; no credentials on devices, and monitor connector usage.
- Harden Identities & Permissions
Grant least-privilege Send As/On Behalf; avoid shared credentials.
Use dedicated mailboxes/service principals for apps; app passwords only if policy permits.
- Monitor and Alert
Track failed SMTP logins, connector hits, and throttling via Message trace and sign-in logs; set alerts in Purview/Defender for anomalies.
- Secure Endpoints
Allow outbound to smtp.office365.com:587; don’t break TLS with interception; log client/device versions and enforce patch baselines.
- Document and Review
Record your Office 365 SMTP settings, connector scopes, and secret/certificate rotations. Run quarterly control reviews and change-control audits.
Office 365 SMTP Sending Limits You Must Know
Use this checklist to lock down SMTP AUTH and connector-based relay in Microsoft 365 while staying compliant and keeping mail flowing.
- Daily sending caps
You can send to up to 10,000 recipients per mailbox in any 24-hour period.
Microsoft may also slow delivery to about 30 messages per minute.
- Recipient limits per message
Each email can include up to 500 recipients across To, Cc, and Bcc.
A distribution list counts as all of its members.
- Relay connector restrictions
Office 365 SMTP relay on port 25 uses your public IP for trust instead of a mailbox sign-in.
Limit it to static trusted IPs and to accepted domains in your tenant.
Throughput depends on tenant policy and sender reputation, and some providers block port 25.
- Workarounds for scale and reliability
For higher volume or cold outreach, use ZapMail for pacing, warm-up, and reporting, or a dedicated email service such as SendGrid or Amazon SES.
Improve consistency by adjusting send cadence, segmenting lists, and splitting traffic so transactional mail stays on Microsoft 365 and campaigns go through the ESP.
Zapmail: An Outreach-Focused Alternative to Office 365 SMTP Relay
ZapMail is built for campaigns and cold outreach, so it takes over when Microsoft 365 limits and basic relay controls start to get in the way.
When to use ZapMail
- High-volume or cold outreach when Exchange Online limits get in the way
- Campaigns that need precise pacing, scheduling, and segmentation
Why it’s better for outreach
- Scalable sending with queueing, throttling, and automatic warm up to protect reputation
- Deliverability tools for bounces, complaints, suppression lists, and open/click tracking
- Analytics with campaign-level metrics to refine content, timing, and list hygiene
How it fits with Office 365
- Send through SMTP AUTH on port 587 with STARTTLS and OAuth2, or use ZapMail as the
primary ESP while Microsoft 365 handles everyday mail - Keep printers and other devices on Microsoft 365 relay over port 25
- Route campaigns and large-scale transactional mail through ZapMail
Office 365 SMTP Relay vs Zapmail for Cold Outreach (Quick Comparison)
Cold outreach quickly runs into Office 365 SMTP relay constraints, IP-based on port 25, ISP blocks, anti-abuse throttling, and no built-in warm-up or analytics.
These limits raise spam risk and make pacing, segmentation, and proof of performance hard.
ZapMail is purpose-built for outreach: OAuth2 SMTP on 587, send pacing, automated warm-up, suppression, and campaign-level reporting.
In short, keep devices on relay, but route cold campaigns through ZapMail for scale and deliverability.
| Feature | Office 365 SMTP Relay | ZapMail |
| Sending limits | 10,000 recipients/day per Microsoft 365 mailbox (and ~30 messages/min for SMTP AUTH; recipient limit commonly 500–1,000/message) | Sending limits are set per mailbox by the provider. Microsoft 365 allows about 10,000 recipients per day and may pace delivery to around 30 messages a minute. Google Workspace allows about 2,000 recipients per day. Capacity grows with the number of mailboxes, so twenty Microsoft 365 mailboxes can reach roughly two hundred thousand recipients in a day. |
| Authentication | Basic / IP-based | OAuth2-ready |
| Deliverability | Depends on DNS (SPF/DKIM/DMARC) | Optimized warm-up + tracking |
| Use case | Devices, small orgs | Cold outreach, campaigns, transactional |
| Integration | Microsoft ecosystem | Microsoft + multi-platform |
| Cost | Included in O365 plan | Affordable SaaS pricing |
Conclusion
Microsoft 365 can be a dependable mail backbone when it is set up with care.
For app driven sending, sign in with SMTP AUTH on port 587 to smtp.office365.com.
Turn on STARTTLS and use OAuth2. Align SPF, DKIM, and DMARC so messages reach the inbox.
Use SMTP AUTH for software that can log in. Use a connector that trusts only your public IPs for printers and other devices.
Avoid running campaigns over relay. For cold outreach, add ZapMail to handle warm up, pacing, reputation, and analytics while Microsoft 365 manages core delivery.
This mix gives you reliable results with clear control.
Get started with ZapMail to build a durable cold email infrastructure alongside your Office 365 setup.
FAQs
Q1 What are the Office 365 SMTP settings?
Use smtp.office365.com on port 587 with STARTTLS and authentication. Prefer OAuth2.
Q2 Should I use port 25 or 587?
Use port 587 for SMTP AUTH. Use port 25 only for Office 365 SMTP relay through a connector.
Q3 How do I enable Authenticated SMTP?
In the Microsoft 365 admin center, go to Users then Active users. Select the mailbox. Open Mail then Manage email apps. Turn on Authenticated SMTP and save. If the option is missing, enable it at the tenant level first.
Q4 Does Office 365 allow SMTP relay?
Yes. Create an Exchange Online connector and restrict it to your trusted public IP addresses.
Q5 Why are my emails going to spam?
Common causes include missing or misaligned SPF, DKIM, or DMARC, a weak sender reputation from sudden volume or poor list hygiene, and message or link content that triggers filters.
Q6 Is Office 365 SMTP secure enough for bulk sending?
Security is strong with TLS and OAuth2, but volume is limited. For higher scale, use ZapMail or a dedicated email service provider to manage pacing, reputation, and reporting.



